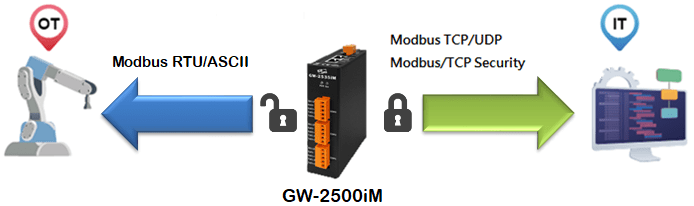
Exploring Modbus Secure: Enhancing Industrial Communication
In the realm of industrial automation and control systems, Modbus has long been a trusted protocol for communication between devices. However, with the increasing connectivity of industrial networks and the rise of cyber threats, ensuring the security of these communications is paramount. This is where Modbus Secure comes into play.
Modbus Secure is an extension of the traditional Modbus protocol that incorporates security features to protect data integrity and confidentiality. By implementing encryption, authentication, and authorization mechanisms, Modbus Secure mitigates the risk of cyber attacks targeting industrial control systems.
One key feature of Modbus Secure is end-to-end encryption, which ensures that data transmitted between devices is secure and cannot be intercepted or tampered with by malicious actors. This encryption layer adds a crucial level of protection to sensitive information exchanged within industrial networks.
Authentication is another vital aspect of Modbus Secure. By requiring devices to authenticate themselves before establishing a connection, this protocol prevents unauthorized access and helps verify the identity of communicating parties. This helps in maintaining the integrity of the network and safeguarding against potential breaches.
Furthermore, Modbus Secure implements robust authorization mechanisms to control access rights within the network. By defining user roles and permissions, administrators can restrict access to critical resources and prevent unauthorised changes to system configurations.
Overall, Modbus Secure represents a significant advancement in securing industrial communication protocols. By integrating encryption, authentication, and authorization capabilities into the traditional Modbus framework, this protocol offers a comprehensive solution for protecting critical infrastructure from cyber threats.
As industries continue to embrace digital transformation and interconnected technologies, implementing robust security measures like Modbus Secure is essential to safeguarding operations and maintaining business continuity in an increasingly complex threat landscape.
Top 7 Tips for Enhancing Modbus Security
- Ensure devices are properly authenticated before allowing Modbus communication.
- Implement secure communication channels such as VPNs for remote Modbus connections.
- Regularly update firmware and software to patch any security vulnerabilities.
- Use strong encryption methods to protect data transmitted over Modbus networks.
- Restrict access to Modbus devices based on the principle of least privilege.
- Monitor Modbus traffic for any unusual or unauthorized activity.
- Train employees on best practices for maintaining Modbus security.
Ensure devices are properly authenticated before allowing Modbus communication.
To enhance the security of Modbus communication within industrial networks, it is essential to ensure that devices are properly authenticated before establishing any connections. By implementing robust authentication mechanisms, such as requiring devices to verify their identities before initiating communication, organisations can prevent unauthorised access and protect sensitive data from potential cyber threats. This proactive approach to device authentication plays a crucial role in maintaining the integrity and confidentiality of Modbus communications, ultimately bolstering the overall security posture of industrial control systems.
Implement secure communication channels such as VPNs for remote Modbus connections.
To enhance the security of remote Modbus connections, it is recommended to implement secure communication channels such as Virtual Private Networks (VPNs). By using VPNs, data transmitted between devices over remote connections is encrypted and protected from potential eavesdropping or tampering by cyber attackers. This additional layer of security ensures that sensitive information exchanged via Modbus protocols remains confidential and secure, mitigating the risks associated with remote access to industrial control systems.
Regularly update firmware and software to patch any security vulnerabilities.
To enhance the security of your industrial communication network using Modbus Secure, it is crucial to regularly update firmware and software to patch any potential security vulnerabilities. By staying up-to-date with the latest updates and patches provided by the software vendors, you can ensure that your system remains resilient against emerging threats and exploits. Regular maintenance and updates play a key role in strengthening the overall security posture of your Modbus Secure implementation, safeguarding your critical infrastructure from potential cyber attacks.
Use strong encryption methods to protect data transmitted over Modbus networks.
When implementing Modbus Secure, it is crucial to utilise strong encryption methods to safeguard data transmitted over Modbus networks. By employing robust encryption techniques, such as AES (Advanced Encryption Standard) or RSA (Rivest-Shamir-Adleman), organisations can ensure that sensitive information remains secure and protected from potential cyber threats. Strong encryption adds a layer of defence against unauthorized access and interception, enhancing the overall security posture of industrial communication systems using the Modbus protocol.
Restrict access to Modbus devices based on the principle of least privilege.
When implementing Modbus Secure, it is crucial to adhere to the principle of least privilege when setting access permissions for devices. By restricting access to Modbus devices based on this principle, only the necessary privileges are granted to users or systems, minimising the risk of unauthorised access and potential security breaches. This approach ensures that each user or system has access only to the specific resources and functions required to perform their designated tasks, enhancing overall security and control within the industrial network environment.
Monitor Modbus traffic for any unusual or unauthorized activity.
To enhance the security of Modbus communication, it is advisable to monitor Modbus traffic for any unusual or unauthorised activity. By actively monitoring the data exchange between devices, operators can quickly detect any anomalies that may indicate a potential security breach. This proactive approach allows for timely intervention to investigate and address any suspicious activities, helping to maintain the integrity and confidentiality of industrial communication networks.
Train employees on best practices for maintaining Modbus security.
To enhance Modbus security within your organisation, it is crucial to train employees on best practices for maintaining the integrity and confidentiality of communication protocols. Educating staff members on the importance of following security protocols, such as using strong passwords, implementing encryption measures, and recognising potential threats, can significantly reduce the risk of cyber attacks targeting Modbus systems. By fostering a culture of awareness and responsibility among employees, organisations can strengthen their overall cybersecurity posture and mitigate potential vulnerabilities in industrial communication networks.
Tags: authentication, authentication protocols, authorization mechanisms, confidentiality, cyber threats, data integrity, encryption, end-to-end encryption, industrial communication, malicious actors, modbus protocol, modbus secure, network security, security features, user roles and permissions