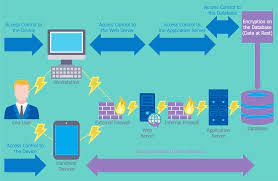
In today’s digital age, network security has become a paramount concern for businesses and individuals alike. With the increasing sophistication of cyber threats, it is essential to invest in robust network security products that can safeguard sensitive information and protect against malicious attacks.
Network security products encompass a wide range of tools and technologies designed to detect, prevent, and mitigate potential risks within a computer network. These products serve as a shield against unauthorized access, data breaches, malware infections, and other cyber threats that can compromise the integrity and confidentiality of valuable data.
One of the key components of network security is a firewall. A firewall acts as a barrier between an internal network and external networks or the internet. It monitors incoming and outgoing network traffic based on predefined rules, allowing only authorized communication while blocking potentially harmful or suspicious activities. Firewalls are available in both hardware and software forms, providing flexibility for different network setups.
Another crucial aspect of network security is antivirus software. This software scans files, programs, and emails for known malware signatures or suspicious behavior patterns. By regularly updating virus definitions, antivirus software can detect and eliminate various types of malware such as viruses, worms, Trojans, ransomware, and spyware. This proactive approach helps prevent infections from spreading throughout the network.
Intrusion Detection Systems (IDS) are another vital component of network security products. IDS monitor network traffic in real-time to identify any unauthorized or suspicious activities that may indicate an intrusion attempt. IDS can be classified into two types: Network-based IDS (NIDS) which analyze traffic at specific points within the network infrastructure, and Host-based IDS (HIDS) which monitor individual devices for signs of compromise.
Virtual Private Networks (VPNs) are widely used to ensure secure remote access to corporate networks or when connecting to public Wi-Fi hotspots. VPNs encrypt data transmitted over untrusted networks by creating a secure tunnel between the user’s device and the destination server. This encryption prevents eavesdropping and protects sensitive information from interception.
In addition to these core network security products, there are many other tools and technologies available to enhance the overall security posture. These include data loss prevention (DLP) solutions, secure email gateways, web content filtering, vulnerability scanners, and network access control systems.
When selecting network security products, it is crucial to consider the specific needs and requirements of your organization. Factors such as network size, complexity, industry regulations, and budget constraints should all be taken into account. It is advisable to consult with a reputable IT security provider or engage the services of a cybersecurity professional to ensure the most appropriate products are chosen.
Investing in robust network security products is not just about protecting sensitive data; it is also about safeguarding your organization’s reputation and maintaining customer trust. By proactively addressing potential threats and vulnerabilities within your network infrastructure, you can significantly reduce the risk of cyberattacks and ensure business continuity.
Remember that network security is an ongoing process that requires regular monitoring, updates, and employee education. By staying vigilant and leveraging the right network security products, you can establish a strong defense against cyber threats and keep your digital assets safe in today’s ever-evolving threat landscape.
Frequently Asked Questions: Network Security Products and Support in the UK
- What network security products are available?
- How do I choose the right network security product for my business?
- What features should I look for when selecting a network security product?
- How can I ensure my network security system is up to date and secure?
- Is there a cost-effective way of protecting my business from cyber threats?
- What support is provided with the purchase of a network security product?
What network security products are available?
There is a wide range of network security products available to address various aspects of network protection. Here are some commonly used network security products:
- Firewalls: Firewalls act as a barrier between an internal network and external networks or the internet. They monitor and control incoming and outgoing traffic based on predefined rules, blocking unauthorized access and potential threats.
- Antivirus Software: Antivirus software scans files, programs, and emails for known malware signatures or suspicious behavior patterns. It helps detect and eliminate viruses, worms, Trojans, ransomware, spyware, and other types of malware.
- Intrusion Detection Systems (IDS): IDS monitor network traffic in real-time to identify unauthorized or suspicious activities that may indicate an intrusion attempt. They can be network-based (NIDS) or host-based (HIDS), providing additional layers of security.
- Virtual Private Networks (VPNs): VPNs create secure encrypted tunnels between a user’s device and a destination server over untrusted networks. They protect data transmitted over public Wi-Fi hotspots or enable secure remote access to corporate networks.
- Data Loss Prevention (DLP) Solutions: DLP solutions help prevent the unauthorized disclosure of sensitive data by monitoring and controlling data flows within the network environment. They can detect and prevent data leaks through various channels like email, web uploads, or removable storage devices.
- Secure Email Gateways: Secure email gateways protect against email-based threats such as spam, phishing attacks, malware attachments, and malicious links. They filter incoming and outgoing emails to ensure secure communication.
- Web Content Filtering: Web content filtering tools restrict access to inappropriate or potentially harmful websites based on predefined policies. They help enforce acceptable use policies within an organization while protecting against web-based threats.
- Vulnerability Scanners: Vulnerability scanners identify weaknesses in networks, systems, applications, or configurations that could be exploited by attackers. They help organizations proactively address vulnerabilities and reduce the risk of exploitation.
- Network Access Control Systems: Network access control systems enforce security policies by regulating access to network resources based on factors such as user identity, device health, and compliance status. They ensure that only authorized and secure devices can connect to the network.
These are just a few examples of network security products available in the market. It’s important to assess your specific needs, consider industry best practices, and consult with experts to determine which combination of products will provide comprehensive protection for your network infrastructure.
How do I choose the right network security product for my business?
Choosing the right network security product for your business is a critical decision that requires careful consideration. Here are some key factors to keep in mind when making your choice:
- Assess your needs: Start by assessing your specific security needs and requirements. Consider factors such as the size of your network, the sensitivity of the data you handle, compliance regulations you must adhere to, and any industry-specific security standards that apply.
- Identify potential threats: Understand the potential threats that your business may face. This could include malware attacks, data breaches, insider threats, or targeted attacks. By identifying these risks, you can prioritize the features and capabilities you need in a network security product.
- Evaluate scalability: Consider whether the network security product can scale with your business as it grows. Ensure that it can handle increasing network traffic and accommodate additional devices or users without compromising performance or security.
- Research reputable vendors: Look for reputable vendors with a proven track record in network security. Read customer reviews and testimonials to gauge their reliability and customer satisfaction levels. Consider their experience in serving businesses similar to yours.
- Understand integration capabilities: Assess how well the network security product integrates with your existing IT infrastructure and other security solutions you may have in place. Compatibility with your current systems will make deployment smoother and more efficient.
- Consider ease of use: Network security products should be user-friendly and intuitive for both IT administrators and end-users. Complex solutions may require extensive training or ongoing technical support, which can add to costs and impact productivity.
- Check for regular updates and support: Ensure that the vendor provides regular updates, patches, and firmware upgrades to address emerging threats effectively. Prompt technical support is crucial in case of any issues or vulnerabilities that may arise.
- Evaluate cost-effectiveness: Compare pricing models among different vendors while considering the value provided by each solution. Remember that investing in robust network security products is an investment in protecting your business and avoiding potential financial losses due to security breaches.
- Seek recommendations and expert advice: Consult with IT professionals or engage the services of a cybersecurity consultant who can provide insights tailored to your business needs. They can help you navigate the complex landscape of network security products and make informed decisions.
- Trial and test: Whenever possible, take advantage of free trials or demos offered by vendors. This allows you to evaluate the usability, performance, and compatibility of the product within your specific environment before making a final decision.
By considering these factors and conducting thorough research, you can choose a network security product that aligns with your business requirements, provides robust protection against threats, and offers scalability for future growth.
What features should I look for when selecting a network security product?
When selecting a network security product, it’s important to consider several key features to ensure that it meets your organization’s specific needs and provides robust protection against cyber threats. Here are some essential features to look for:
- Firewall capabilities: A network security product should include a firewall component that can effectively control incoming and outgoing network traffic based on predefined rules. Look for features such as advanced packet inspection, application-level filtering, and the ability to create custom rule sets.
- Intrusion Detection and Prevention System (IDS/IPS): An IDS/IPS is crucial for detecting and preventing unauthorized access attempts or suspicious activities within your network. Look for a product that offers real-time monitoring, signature-based detection, anomaly detection, and the ability to block or mitigate identified threats.
- Antivirus and malware protection: Ensure that the network security product includes robust antivirus and anti-malware capabilities. It should provide regular updates to virus definitions, heuristic scanning techniques to detect unknown threats, and the ability to quarantine or remove infected files.
- Virtual Private Network (VPN) support: If your organization requires secure remote access or connects to public Wi-Fi networks frequently, look for a network security product that supports VPN functionality. This feature encrypts data transmitted over untrusted networks, ensuring privacy and preventing unauthorized access.
- Web content filtering: To protect against web-based threats such as malicious websites or inappropriate content, consider a network security product with web content filtering capabilities. This feature allows you to block access to specific categories of websites or URLs based on predefined policies.
- Data loss prevention (DLP): DLP features help prevent sensitive data from leaving your network without authorization. Look for a product that offers data classification, policy enforcement, encryption options, and monitoring capabilities to detect potential data leaks.
- Centralized management: Managing network security across multiple devices can be complex. Look for a solution with centralized management capabilities that allow you to configure, monitor, and update security policies from a single console. This feature streamlines administration and enhances overall network security.
- Scalability and performance: Consider the scalability of the network security product to ensure it can handle your organization’s current and future needs. Look for features that support high-performance networks, such as load balancing, clustering, and the ability to handle increasing traffic volumes without compromising security.
- Reporting and analytics: Effective network security requires visibility into threats, vulnerabilities, and network activity. Look for a product that provides comprehensive reporting and analytics capabilities, allowing you to monitor trends, identify potential risks, and make informed decisions to strengthen your security posture.
- Vendor reputation and support: Lastly, consider the reputation of the vendor behind the network security product. Look for established vendors with a track record of delivering reliable products and providing excellent customer support. Read reviews, seek recommendations from trusted sources, and evaluate the vendor’s commitment to regular updates and addressing vulnerabilities.
By considering these essential features when selecting a network security product, you can ensure that it aligns with your organization’s requirements and provides robust protection against cyber threats.
How can I ensure my network security system is up to date and secure?
Ensuring that your network security system is up to date and secure is crucial in today’s rapidly evolving threat landscape. Here are some steps you can take to maintain the effectiveness of your network security:
- Regularly update software and firmware: Keep all your network security products, including firewalls, antivirus software, and intrusion detection systems, up to date with the latest patches and updates. These updates often include critical security fixes that address known vulnerabilities.
- Implement strong access controls: Use strong passwords or passphrase combinations for all network devices and regularly change them. Additionally, enable multi-factor authentication (MFA) wherever possible to add an extra layer of protection.
- Conduct regular security audits: Perform periodic assessments of your network infrastructure to identify any potential vulnerabilities or misconfigurations. This can include penetration testing, vulnerability scanning, and reviewing access controls.
- Monitor network traffic: Utilize network monitoring tools to actively monitor inbound and outbound traffic for any suspicious activities or anomalies. This can help detect potential threats early on and allow for timely response.
- Employ intrusion detection/prevention systems: Implement intrusion detection systems (IDS) or intrusion prevention systems (IPS) to monitor your network for any unauthorized access attempts or malicious activities. These systems can provide real-time alerts and help prevent potential breaches.
- Educate employees about cybersecurity best practices: Human error is one of the leading causes of security breaches. Train your employees on safe browsing habits, email phishing awareness, password hygiene, and other cybersecurity best practices to minimize the risk of accidental data breaches.
- Regularly back up critical data: Implement a robust backup strategy that includes regular backups of critical data stored within your network infrastructure. This ensures that even if a breach occurs, you can quickly recover important information without paying ransomware demands or suffering significant data loss.
- Stay informed about emerging threats: Stay updated on the latest cybersecurity news, trends, and emerging threats relevant to your industry. This knowledge will help you proactively adapt your network security measures to address new and evolving risks.
- Engage with a trusted security provider: Consider partnering with a reputable cybersecurity provider or consultant who can assess your network security posture, provide recommendations, and assist with implementing advanced security measures.
- Regularly review and update security policies: Continuously evaluate and update your organization’s security policies to reflect the evolving threat landscape and changing business needs. Ensure that all employees are aware of these policies and adhere to them.
By following these practices, you can significantly enhance the security of your network infrastructure and reduce the risk of cyber threats. Remember that network security is an ongoing effort that requires constant monitoring, updates, and adaptation to stay ahead of potential risks.
Is there a cost-effective way of protecting my business from cyber threats?
Yes, there are several cost-effective ways to protect your business from cyber threats. Here are some strategies to consider:
- Employee Training: Educating your employees about cybersecurity best practices is one of the most effective and affordable ways to enhance your organization’s security. Conduct regular training sessions to raise awareness about common threats such as phishing emails, social engineering, and password hygiene. Encourage employees to report suspicious activities and provide them with resources to stay informed about the latest security practices.
- Strong Password Policies: Implementing strong password policies is a simple yet powerful measure to protect your business. Encourage employees to use unique and complex passwords for their accounts and enforce regular password changes. Consider implementing multi-factor authentication (MFA) for an added layer of security.
- Regular Software Updates: Keeping your operating systems, applications, and security software up to date is crucial for maintaining a secure environment. Software updates often include important security patches that address vulnerabilities exploited by cybercriminals.
- Firewall Protection: Deploying a firewall is an essential step in securing your network infrastructure. Many routers come with built-in firewalls that can be configured to filter incoming and outgoing traffic based on predefined rules. This provides an additional layer of protection against unauthorized access attempts.
- Antivirus/Antimalware Software: Invest in reputable antivirus or antimalware software for all devices within your organization’s network. There are many cost-effective options available that offer robust protection against malware threats.
- Data Backup and Recovery: Regularly backing up critical data is crucial in case of a ransomware attack or data loss incident. Cloud-based backup solutions can provide cost-effective and secure offsite storage options.
- Network Monitoring: Implementing network monitoring tools can help detect unusual activities or potential security breaches in real-time. These tools can provide alerts and insights into network traffic patterns, allowing you to respond quickly to any potential threats.
- Vendor Security Assessments: If your business relies on third-party vendors or service providers, conduct regular security assessments to ensure they have appropriate security measures in place. This helps minimize the risk of a cyber incident originating from a weak link in your supply chain.
- Incident Response Plan: Develop an incident response plan that outlines the steps to be taken in case of a cybersecurity incident. Having a well-defined plan can help minimize the impact of an attack and facilitate a swift recovery.
Remember, while cost-effective measures can significantly enhance your security posture, it is essential to regularly assess and review your cybersecurity strategy to adapt to evolving threats. Consider consulting with cybersecurity professionals who can provide tailored advice based on your organization’s specific needs and budget constraints.
What support is provided with the purchase of a network security product?
When purchasing a network security product, it is common for vendors to provide various forms of support to ensure customers can effectively implement and utilize the product. The specific support offerings may vary depending on the vendor and the product purchased, but here are some common types of support typically provided:
- Technical Support: Most vendors offer technical support services to assist customers with any issues or questions they may encounter during the installation, configuration, or usage of the network security product. This support is usually available through phone, email, or an online ticketing system. Technical support teams are trained to troubleshoot problems and provide guidance to resolve issues promptly.
- Software Updates and Patches: Network security products require regular updates to address emerging threats and vulnerabilities. Vendors typically provide software updates, bug fixes, and security patches to keep their products up-to-date. These updates often include new features, performance improvements, and enhancements based on customer feedback.
- Documentation and Knowledge Base: Vendors usually provide comprehensive documentation such as user manuals, installation guides, configuration instructions, and troubleshooting tips. Additionally, many vendors maintain a knowledge base or an online resource center where customers can access articles, tutorials, FAQs (Frequently Asked Questions), and best practices to help them maximize the value of their network security product.
- Training Materials: Depending on the complexity of the network security product, vendors may offer training materials in various formats like videos or webinars to help users understand how to effectively use the product’s features and functionalities. These training resources can empower customers to make the most out of their investment by utilizing all available capabilities.
- Community Forums or User Groups: Some vendors facilitate online forums or user groups where customers can interact with each other and exchange knowledge about the network security product. These communities provide an opportunity for users to share experiences, ask questions, learn from others’ insights, and even receive unofficial assistance from fellow users.
It is important to note that the level and extent of support provided may differ based on factors such as the type of product, license agreement, and service level agreements. Some vendors may offer additional premium support options for customers who require more dedicated assistance or faster response times.
Before purchasing a network security product, it is advisable to review the vendor’s support offerings to ensure they align with your organization’s needs and expectations. Understanding the available support channels and resources can help you make an informed decision and ensure a smooth implementation and usage experience.
Tags: antivirus software, data loss prevention solutions, firewalls, intrusion detection systems, network access control systems, network security products, secure email gateways, virtual private networks, vulnerability scanners, web content filtering